Description
Overview
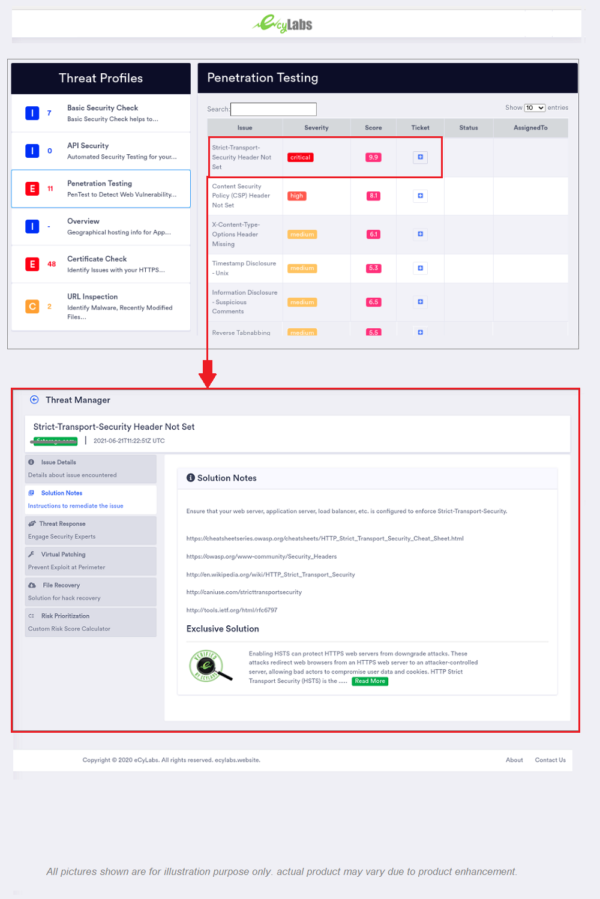
Penetration testing helps to identify malicious behaviours or patterns by simulating an external attacker’s view. In the context of web application security, pen testing is commonly used to augment a web application firewall (WAF). eCyLabs Pen testing scan profiles leveraging OWASP Detection Logics and its widely used, often in conjunction with connected systems such as servers, networks, devices, to endpoints.
Many of the security flaws in the OWASP Top 10 list can be identified with our tool such as,
– Injection
– Broken authentication
– Sensitive data exposure
– XML external entities (XXE)
– Broken access control
– Security misconfigurations
– Cross site scripting (XSS)
– Insecure deserialization
– Using components with known vulnerabilities
– Insufficient logging and monitoring
Pen testing follows with below stages:
- Explore – The tester attempts to learn about the system being tested. This includes trying to determine what software is in use, what endpoints exist, what patches are installed, etc. It also includes searching the site for hidden content, known vulnerabilities, and other indications of weakness.
- Attack – The tester attempts to exploit the known or suspected vulnerabilities to prove they exist.
- Report – The tester reports back the results of their pen test including the vulnerabilities, how they exploited them and how difficult the exploits were, and the severity of the exploitation.