Description
OWASP Top 10 API Security Testing
eCyLabs API Security scanner leveraging OWASP Detection Logics and provides security testing for web application APIs. It helps to Detect flows to protect APIs from Man in the middle attacks. They enable access to sensitive software functions and data, so they are becoming a primary target for attackers. Companies use web APIs to connect web services and transfer data between applications. The applications will also interchange a high volume of valuable and sensitive information. The APIs that are broken, disclosed or hacked can reveal sensitive information like medical, financial or even personal data. When it approaches to verify the Web API security, you require proper strategies for the authentication and authorization.
APIs are vulnerable to attack. The impact of API security breaches goes with financial costs, legal battles, fines, and lost customers.
OWASP added the API Security Top 10 list that need to be addressed:
– Broken Object Level Authorization
– Broken Authentication
– Excessive Data Exposure
– Lack of Resources & Rate Limiting
– Mass Assignment
– Security misconfigurations
– Injection
– Improper Assets Management
– Insufficient Logging & Monitoring
API testing follows with below stages:
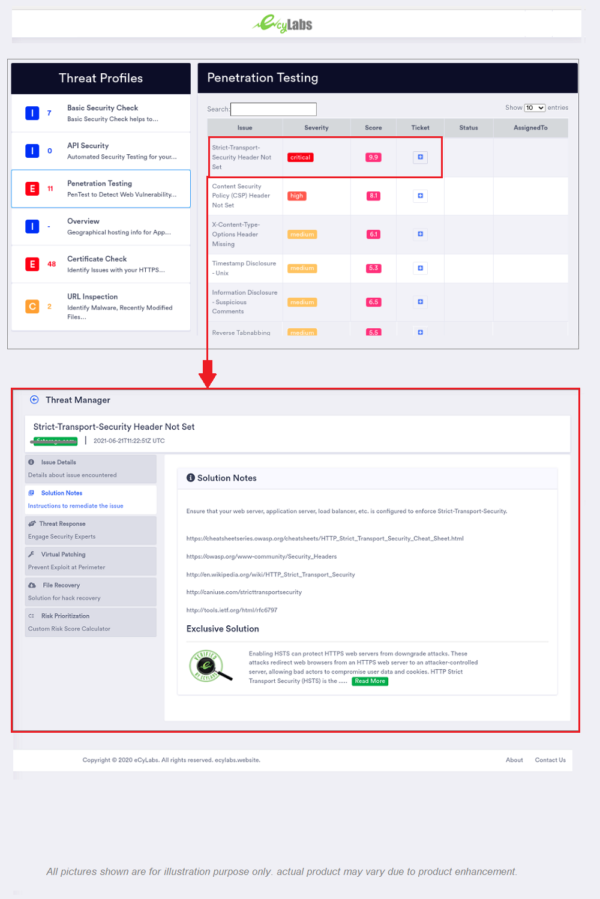
- Vulnerability assessment: Performing automated penetration testing for your APIs can permit you to identify vulnerabilities at the proper time and you can fix them accordingly.
- Authorization: Authenticating API traffic using OAuth and JSON Web Tokens allows you to set access control rules to particular API resources.
- Encryption: Using TLS is best practice for encrypting the data for API protection. It requires a Signature to decrypt and modify the data. It can help users from the risk of man-in-the-middle-attacks.
Using an API gateway: An API gateway allows you to keep track of all API calls and do the necessary monitoring to understand how the API utilization happens.