
A California-based Connectivity Management company, specializing in AI-driven Quality of Experience (QoE) platforms for challenging environments like maritime, aviation, and remote locations, sought to enhance its information security posture. Given the complexity of their satellite-reliant network systems, they aimed to achieve ISO 27001 certification to demonstrate to clients and partners their commitment to robust data protection. This case study details how, in partnership with eCyLabs, they successfully navigated the certification process, leveraging eCyLabs' expertise to strengthen their security framework and build client trust.
By engaging and guiding various teams, and focusing on risk mitigation, we ensured compliance and achieved the desired certification, strengthening the organizations security foundation. Successfully achieved ISO 27001 certification, demonstrating the organizations commitment to information security.

A leading British Bank sought to optimize its management of third-party connections across its global operations. The objective was to consolidate support under a central team, implement a unified database, establish standardized support processes and service level agreements (SLAs), and develop a cohesive global support strategy. eCyLabs provided strategic advisory and played a key role in the product design, enabling the bank to manage its third-party connections independently through seamless integration of multiple internal platforms. This case study details how the bank, with eCyLabs' support, achieved significant efficiency gains and improved service consistency by centralizing and standardizing its third-party connection management.
Behalf authorized vendor eCyLabs proposed an end-to-end support model in terms of people, process and technology including Market research and provided insight about overall tools that required to run third-party lifecycle, A detailed control matrix documented with roles and responsibilities of teams involved and evaluation of tools for third-party connections management.

A prominent real estate development company in Saudi Arabia sought to strengthen its cybersecurity framework and achieve compliance with the National Cybersecurity Authority's (NCA) Essential Cybersecurity Controls (ECC). Through strategic advisory from authorized vendor, eCyLabs provided advisory to successfully implement the NCA ECC framework, significantly enhancing its security posture and mitigating potential cyber risks. This case study details the process and outcomes of this critical compliance and security initiative.

A major Middle East airport engaged an independent consultant to assess its existing Security Information and Event Management (SIEM) solution, including its disaster recovery (DR) setup. The engagement involved identifying key technology and process gaps, providing actionable recommendations, and developing a transformation program to address critical issues. This case study demonstrates how the airport significantly improved its SIEM performance and strengthened its overall security resilience.
Conducted detailed assessment of existing SIEM deployment including DR setup, processes, capabilities, architecture, and stakeholder interview and business case analysis. Produced recommendation report to business executive that helps to take informed business decision to realize the returns from existing investment and keep the business secure from attack vectors. Proposed transformation program to re-design the architecture, enable advanced use cases, documentation of SOC processes, run books and standard operating manuals.

To ensure the security and reliability of our Business Communications Platform's services within India, a comprehensive Vulnerability Assessment and Penetration Testing (VAPT) project will be conducted on the supporting telecommunication infrastructure; this initiative aims to proactively identify and mitigate potential security weaknesses, ensure compliance with relevant regulations, and safeguard sensitive data, ultimately strengthening the platform's security posture and building trust with our Indian user base.

eCyLabs successfully implemented Okta Universal Directory, seamlessly integrating G-Suite, Jira Suite, BitBucket, and Zoom. This project involved a thorough impact analysis, robust Single Sign-On (SSO) integration and configuration, and rigorous User Acceptance Testing (UAT) with post-check confirmation, ensuring a secure and streamlined user experience across all platforms.

eCyLabs, a Google Cloud Partner, delivered a comprehensive Google Workspace optimization for our client, significantly enhancing security and streamlining operations. By implementing Google Workspace best practices, we proactively mitigated online threats and optimized mail flow. A meticulous cost analysis enabled a strategic downgrade from Enterprise to Business Standard, while maintaining all critical requirements. This transition, coupled with the consolidation of communication tools by leveraging advanced Google Meet and Chat features (replacing Zoom and Slack), resulted in substantial annual savings of $40,000 USD. Furthermore, we implemented Shared Drives for robust file access control and ownership, ensuring data security and efficient collaboration.
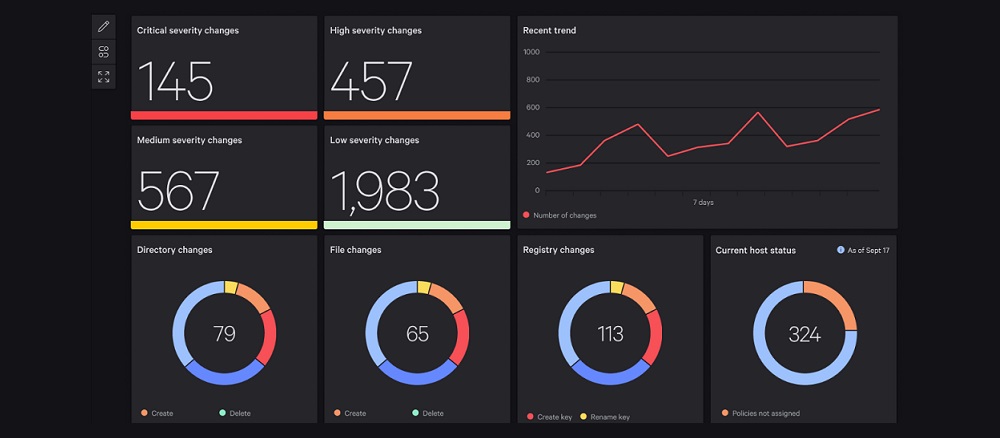
eCyLabs collaborated closely with CrowdStrike engineering and compliance teams to deliver a customized security solution tailored to our client unique needs. We designed and implemented specific security controls, and developed customized dashboards for comprehensive visibility across both remote and on-premises resources. By leveraging CrowdStrike Falcon® platform, we provided instant visibility and robust endpoint protection, effectively preventing attacks regardless of network location.
Design & Develop Cyber security CoE Lab Infrastructure equipped to offer services including forensics, ethical hacking and cyber range programs .Develop knowledge base for the students to undergo basic trainings.
Due diligence helps to identify the key outcomes, objectives and budget considerations .Plan, design, deployment, configuration of solution components to offer programs such as forensics, ethical hacking and cyber range trainings. Development of course schedule, lab run books, auto provision, orchestration and API integration of cyber security applications for ease of use purpose. Auto decommission of virtual machines post completion of course modules.

eCyLabs was engaged to investigate data theft in Structural Company, eCyLabs focused on collecting and analysing data from computer systems to track user-based activity including possibility of user upload to cloud storage services.